In March 2025, a Reddit user raised a familiar question for many DevOps, security teams, and enterprises: Which Kubernetes security stack actually covers most security risks?
Source: Reddit.com
The discussion that followed lacked depth and practical guidance. This article fills that gap by breaking down the most trusted Kubernetes security tools for 2026, based on real-world usage, expert reviews, and community feedback from platforms like Reddit, LinkedIn, and G2.
Portainer: Best for Secure & Governed Kubernetes Management
Portainer provides a controlled, safe platform for managing Kubernetes at scale. It centralizes RBAC, policy enforcement, image controls, and audit logs in a single interface. The platform helps prevent misconfigurations, blocks risky actions, and keeps operations secure while running as a lightweight management layer on your own infrastructure.
Key Features
Portainer helps you control what gets deployed and tracks every action. Here are some of its features that make Kubernetes security possible:
Centralized RBAC and Access Governance

Portainer gives you a clear, centralized way to control who can access clusters, namespaces, and resources. You can assign least-privilege roles, restrict high-risk actions, and keep all permissions consistent across environments. These features reduce accidental changes and strengthen overall governance.
Image and Registry Controls
Portainer allows you to manage access to your registries, blocking untrusted images from being deployed.
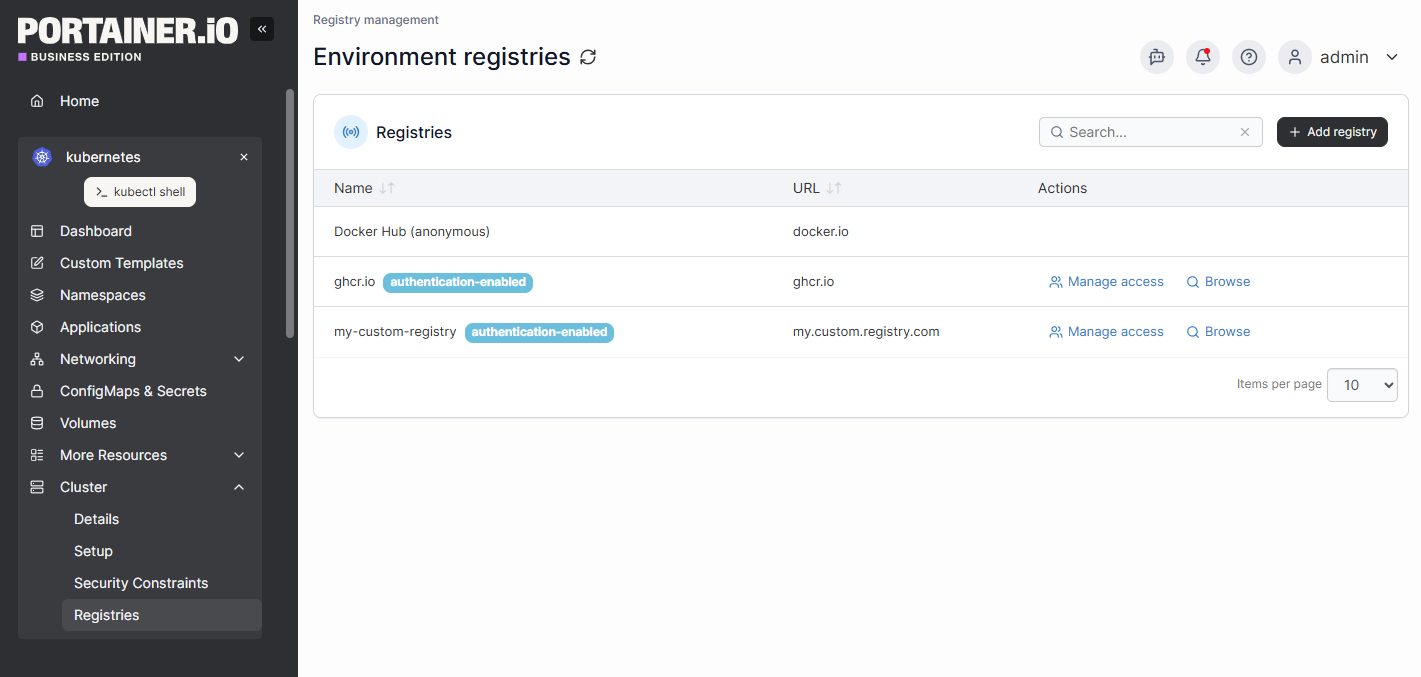
These controls prevent risky images from reaching production and help your team maintain a clean, compliant supply chain.
Full Audit Trails and Activity Tracking
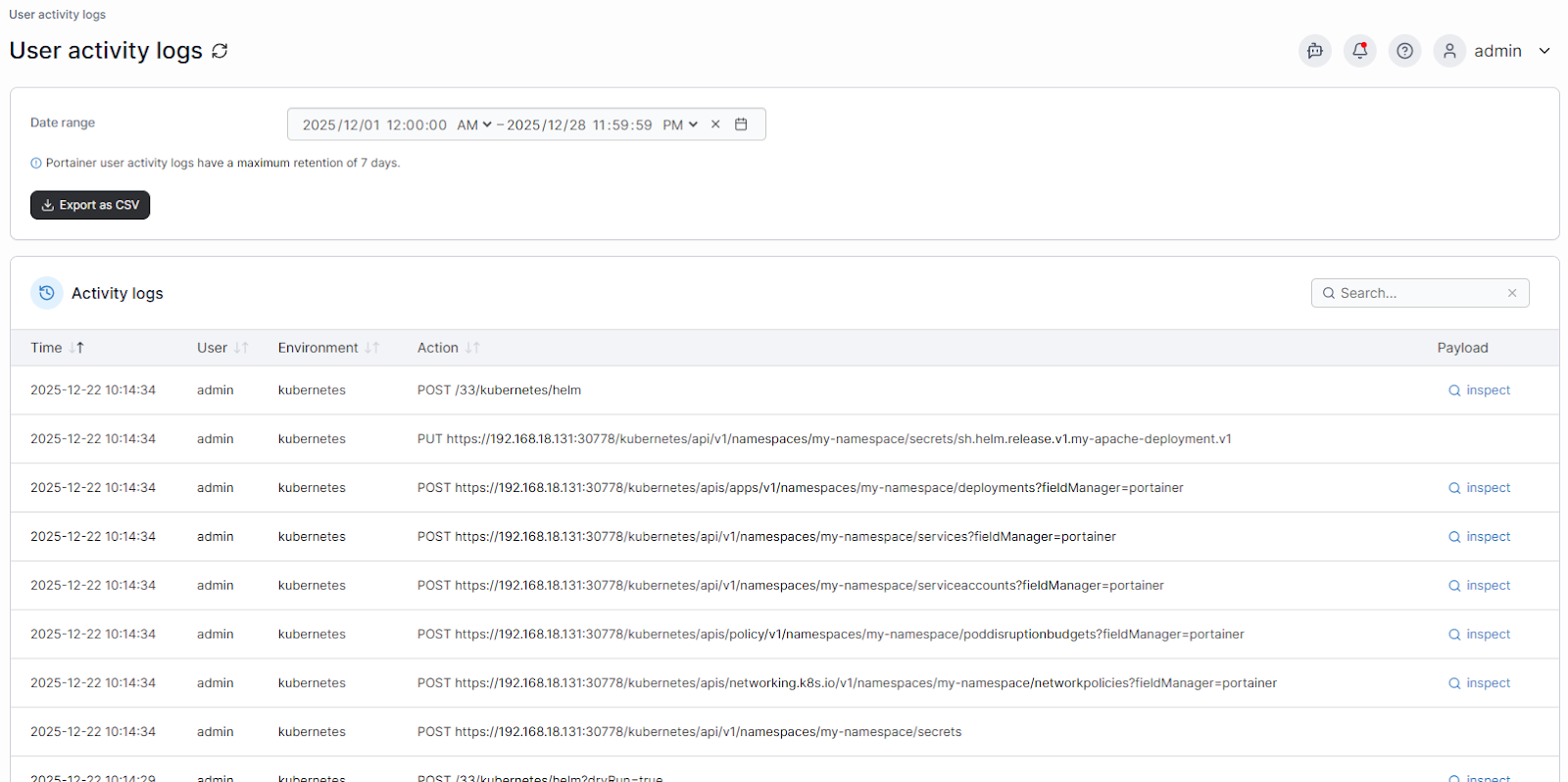
Portainer logs every action taken across clusters, users, and resources. These audit trails help you detect unusual behavior, investigate incidents quickly, and prove compliance during reviews. The visibility also reduces operational stress because teams no longer need to guess what changed or why.
Pricing
Pricing changes per the number of nodes
Note: You can get an extended enterprise free trial with 15 nodes to test the platform on a larger environment for 45 days. You can also sign up for Portainer's managed platform services to help set up and manage your container infrastructure.
Where Portainer Shines
- Strong access control and governance: Portainer centralizes RBAC, policies, and user permissions, allowing teams to keep Kubernetes environments controlled and compliant without juggling multiple tools.
- Clear visibility across clusters: The platform surfaces actions, changes, and deployments in one place, reducing errors and enabling faster security reviews.
- Lightweight management layer: Portainer runs as a single, secure container on your infrastructure, providing a safer operational model than heavier Kubernetes security platforms.
Where Portainer Falls Short
- Not ideal for teams needing deep threat detection: Portainer is not a runtime security engine, so advanced threat analytics and behavioral monitoring require pairing it with another Kubernetes security tool.
- Best suited for teams that want governance, not full outsourcing: It does not offer hosted infrastructure, which benefits teams that prefer control but may not fit those seeking fully managed Kubernetes security software.
{{article-pro-tip}}
Reviews
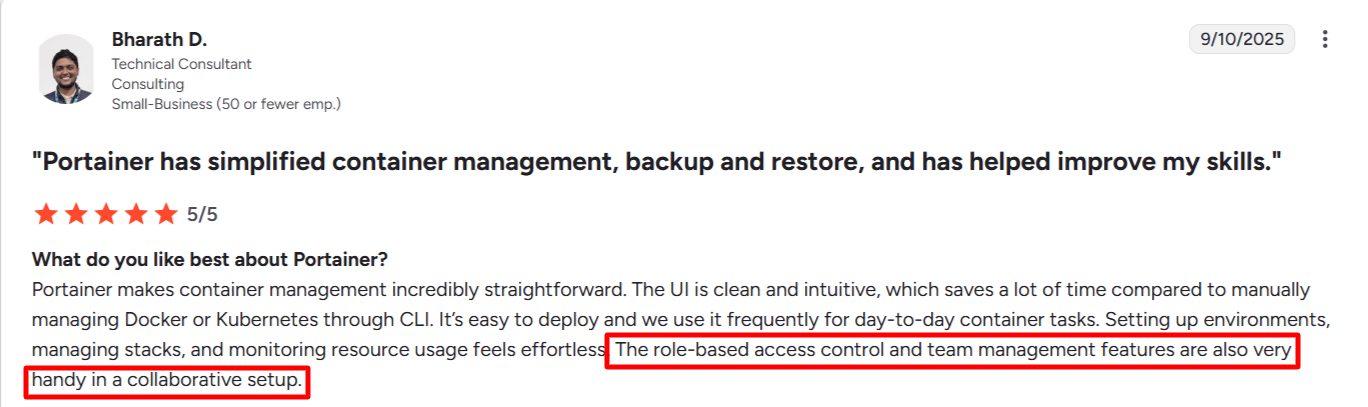
As seen on the Portainer vs. Red Hat OpenShift G2 comparison page, Portainer scores 9.4 for access control, compared to OpenShift's 8.5. Reviewers praise Portainer for providing granular control over user permissions, making it easier to manage security in Kubernetes deployments, while noting OpenShift's features can be more complex.
Source: G2
Also, a global energy company faced challenges with its initial Kubernetes management platform. It was expensive to maintain, inefficient in operation, and insecure.
The energy company specifically wanted an easy-to-use platform that could unify their environments, enforce security policies, and reduce operational overhead without sacrificing performance or control.
Then they switched to Portainer.
Portainer helped the company reduce the complexity of Kubernetes management, replace a costly in-house solution with a scalable, enterprise-grade platform, and strengthen security and access control across multi-cluster environments.
Read the complete case study to see how they achieved premium Kubernetes security with Portainer.
Who Portainer is Best for
- Enterprise platform teams: Teams running multiple Kubernetes clusters that need strong access control, governance, and security guardrails without sacrificing operational control or flexibility.
Book a demo to see why industry-leading enterprises choose Portainer as their Kubernetes management tool, with strong security features on top.
Aqua Security: Best for end-to-end Kubernetes Workload Protection
Aqua Security is a full-spectrum Kubernetes security platform designed to secure containerized applications from development through runtime. It combines posture assessment, workload protection, policy enforcement, and compliance reporting into a single solution.
Aqua helps teams identify and block vulnerabilities before deployment. It also detects and stops active threats in running Kubernetes environments.
Key Features
- Container image scanning: Scans images for vulnerabilities and misconfigurations before deployment.
- Runtime protection: Monitors running containers and blocks suspicious behavior in real time.
- Policy enforcement: Applies security policies across build, deploy, and runtime stages.
- Compliance reporting: Supports common regulatory frameworks and audit requirements.
Pricing
Where Aqua Security Shines
- Broad security coverage: Aqua addresses build-time, deployment-time, and runtime risks on a single platform.
- Strong runtime controls: Real-time enforcement helps stop threats that bypass static scans.
- Enterprise readiness: Designed for regulated industries with mature security teams.
Where Aqua Security Falls Short
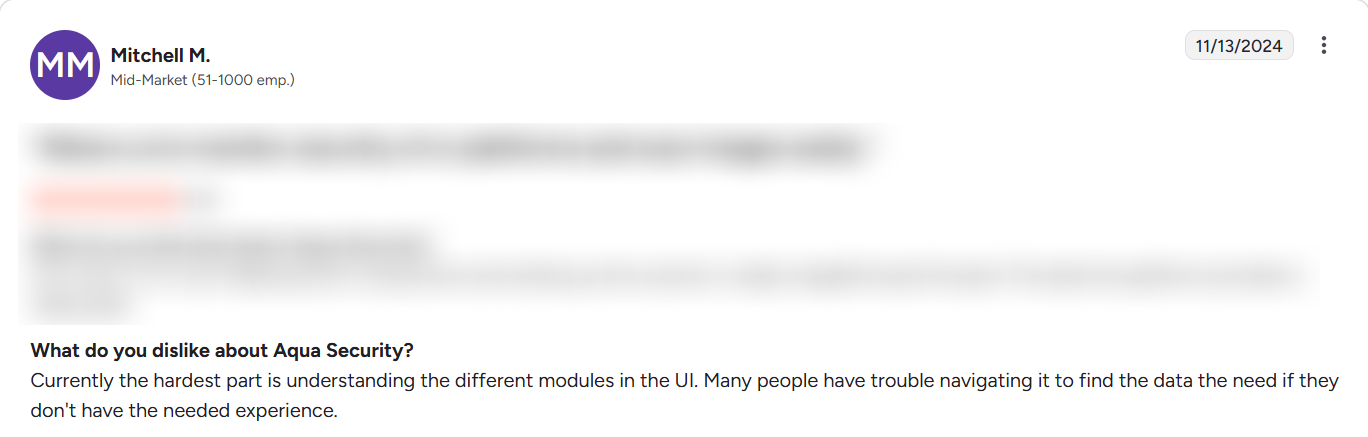
- Operational complexity: The platform can feel heavy for teams without dedicated security ownership.
Source: G2
- Cost at scale: Pricing may be difficult to justify for smaller environments or early-stage teams.
- Less focus on governance workflows: Access control and day-to-day operational governance are not its primary strengths compared to governance-first Kubernetes security tools.
Pro tip: If Aqua's operational depth feels heavy, you can pair it with Portainer to simplify day-to-day Kubernetes security workflows. Portainer's intuitive interface makes access control, governance, and visibility easier to manage.
Customer Reviews
Source: G2
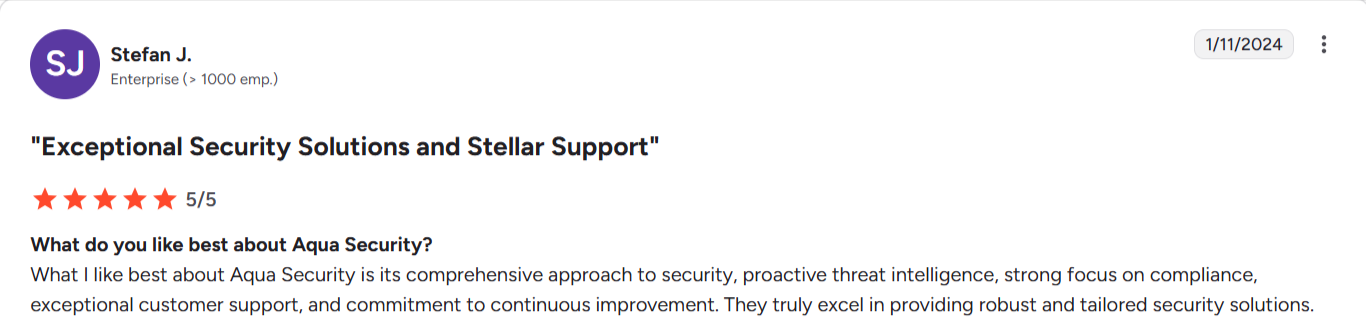
"Aqua's interface can be a little complex at times, and the initial setup requires some technical expertise and loads of document reading." Verified user
Who is Aqua Security Best for
- Enterprise security teams: Organizations running Kubernetes at scale that need deep workload protection, runtime enforcement, and compliance controls as part of a full Kubernetes security platform.
Anchore Enterprise: Best for Pre-Deployment Kubernetes Workload Security
Anchore Enterprise is a Kubernetes security platform built for teams that want to control what enters their clusters before it ever runs. Instead of reacting to runtime threats, it focuses on image assurance, policy enforcement, and supply chain visibility.
Anchore helps you block vulnerable or non-compliant images early, reducing risk long before workloads reach production.
Key Features
- Deep image analysis: Anchore inspects container images for vulnerabilities, secrets, and unsafe packages before deployment.
- Policy-based enforcement: Custom policies block non-compliant images from being promoted across environments.
- Supply chain security: Software bill of materials (SBOM) support improves transparency and audit readiness.
- CI pipeline integration: Scans run early to reduce production risk and rework.
Pricing
Anchore Enterprise follows an enterprise pricing model based on scale and usage.
Where Anchore Enterprise shines
- Strong supply chain focus: Anchore is a solid Kubernetes security tool for teams prioritizing image integrity and provenance.
- Compliance-driven workflows: Policy enforcement supports regulated environments with strict audit needs.
- Shift-left security: Early scanning reduces vulnerabilities before workloads ever reach a cluster.
Where Anchore Enterprise falls short
- Limited runtime protection: Anchore focuses on pre-deployment security rather than live-workload behavior.
- Narrow operational scope: Day-to-day cluster governance and access control fall outside its core design.
- Requires complementary tools: Teams often pair it with broader Kubernetes security solutions to cover runtime and governance gaps.
{{article-cta}}
Customer Reviews
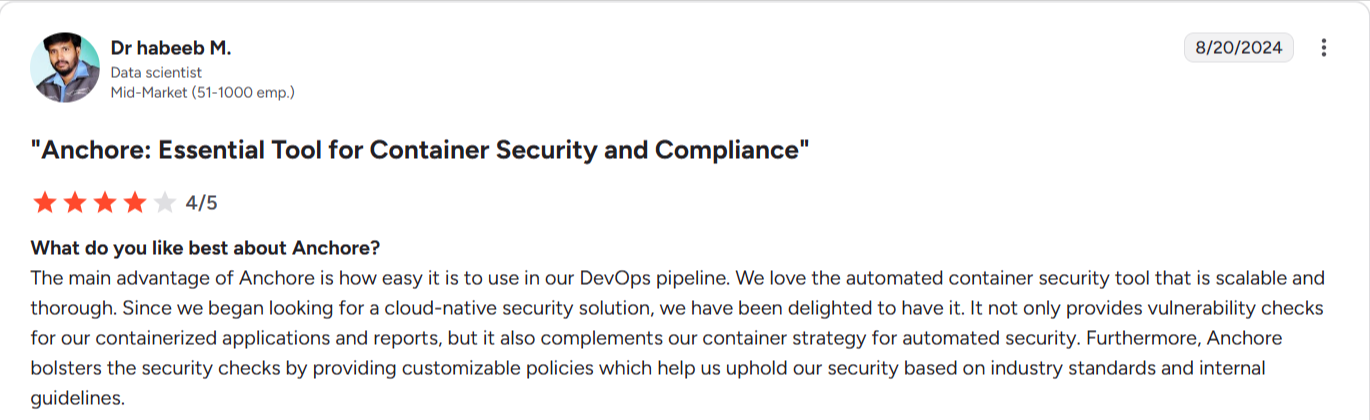
Source: G2
"SBOM takes time to load, but otherwise the information is good." Raja A
Who is Anchore Enterprise best for
- Security and platform teams: Organizations that prioritize container image assurance, supply chain security, and policy enforcement before workloads reach Kubernetes clusters.
Falco: Best for Kubernetes Runtime Threat Detection
Falco is an open source Kubernetes security tool focused on runtime protection. It detects suspicious behavior inside containers, nodes, and workloads by monitoring system calls in real time. Security teams rely on Falco to catch threats that static Kubernetes security software often misses.
Key Features
- Real-time runtime detection: Falco monitors container and node activity to detect abnormal behavior as it happens, not after damage is done.
- Rule-based security policies: Security teams can define rules to flag unexpected file access, privilege escalation, or network activity.
- Cloud-native integrations: Falco integrates with Kubernetes audit logs, SIEM tools, and alerting systems, making it easier to fit into existing Kubernetes security platforms.
Pricing
Where Falco Shines
- Deep runtime visibility: Falco excels at detecting live threats inside running containers, which many Kubernetes security solutions do not cover.
- Strong open-source adoption: As one of the most trusted open-source Kubernetes security tools, Falco benefits from a large, active community.
- Flexible alerting: Alerts can be routed to security and ops tools already used by platform teams.
Where Falco Falls Short
- No built-in governance or access control: Falco focuses on detection, not RBAC, policy management, or cluster governance.
- Alert tuning requires expertise: Poorly tuned rules can create noise, which adds operational load for teams under pressure.
- Limited prevention: Falco detects threats but does not block actions by default, so the response still relies on human or external tooling.
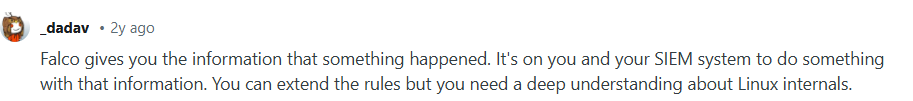
Pro tip: Portainer offers centralized RBAC, access governance, and audit controls to strengthen your Kubernetes security infrastructure.
Customer Reviews
"As a security analyst. I like its powerful intrusion-detection feature, which detects suspicious activity. Also, it is open-source, so it can be used for free." Mansi S.
"Although Falco provides customizable rules, setting up and fine-tuning these rules can be complex, especially for organizations with specific or intricate security requirements. New users might find the initial configuration overwhelming." Bikash S
Who Falco is best for
- Security teams: Teams focused on detecting live threats and suspicious container behavior in production Kubernetes environments.
- Platform engineers: Teams that want runtime visibility as part of a broader Kubernetes security platform.
- Organizations using open source Kubernetes security tools: Teams comfortable with tuning rules and managing alerts internally.
Nutanix Kubernetes Platform: Best for Infrastructure-Centric Enterprise Security
Nutanix Kubernetes Platform (NKP) focuses on securing Kubernetes, where infrastructure control matters most. It combines cluster lifecycle management with network segmentation, identity controls, and policy-driven governance. These features make NKP a strong option for enterprises that want Kubernetes security tightly integrated with their virtualization, networking, and hybrid or on-premise Kubernetes infrastructure stack.
Key Features
- Integrated identity and access controls: Nutanix ties Kubernetes access into enterprise IAM and directory services, helping teams enforce consistent RBAC and authentication policies.
- Network microsegmentation: Built-in networking controls limit east-west traffic and reduce the blast radius of compromised workloads.
- Policy-driven cluster governance: Security policies are applied at the infrastructure and cluster layers, helping standardize controls across environments.
Pricing
Where Nutanix Shines
- Strong infrastructure-level security: Security controls extend beyond the cluster into networking and virtualization
- Good fit for on-prem and hybrid environments: Works well where Kubernetes security solutions must align with existing data center investments.
- Centralized platform approach: Reduces tool sprawl by consolidating infrastructure and Kubernetes security software into a single ecosystem.
Where Nutanix Falls Short
- Less flexible for heterogeneous stacks: Organizations running mixed Kubernetes distributions may find tighter coupling restrictive compared to vendor-agnostic Kubernetes security platforms.
- Higher operational overhead: The platform is powerful but heavier than many open-source Kubernetes security tools.
- Licensing and renewals can be difficult to manage: Feedback from Reddit users highlights overly complex licensing models and confusion around renewal timelines, especially between hardware support and software subscriptions.
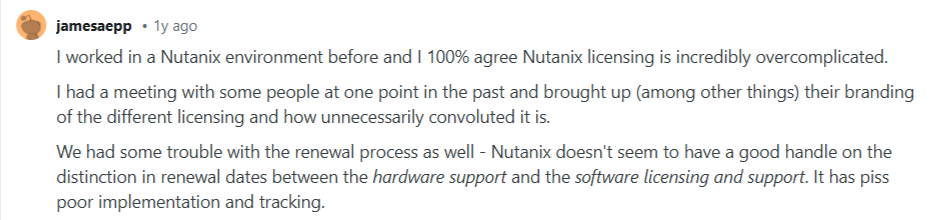
Source: Reddit.com
Customer Reviews

Source: G2
Who NKP is best for
- Large infrastructure-led enterprises: Organizations already invested in Nutanix that want Kubernetes security tightly coupled with on-prem or hybrid infrastructure and centralized platform governance.
How to Choose the Best Kubernetes Security Tool
Not every Kubernetes security tool solves the same problem. The right choice depends on how well a platform protects Kubernetes clusters, supports your engineers, and scales without adding operational fatigue.
Let's see the key features to look out for in any Kubernetes security platform:
Access Control and Governance
A strong Kubernetes security platform enforces least privilege, supports namespace-level roles, and makes permissions easy to audit.
Centralized governance reduces mistakes and limits the blast radius during incidents. Portainer handles this well by managing RBAC, users, and teams from one interface across clusters. You can also add, remove, or manage namespaces on Portainer.
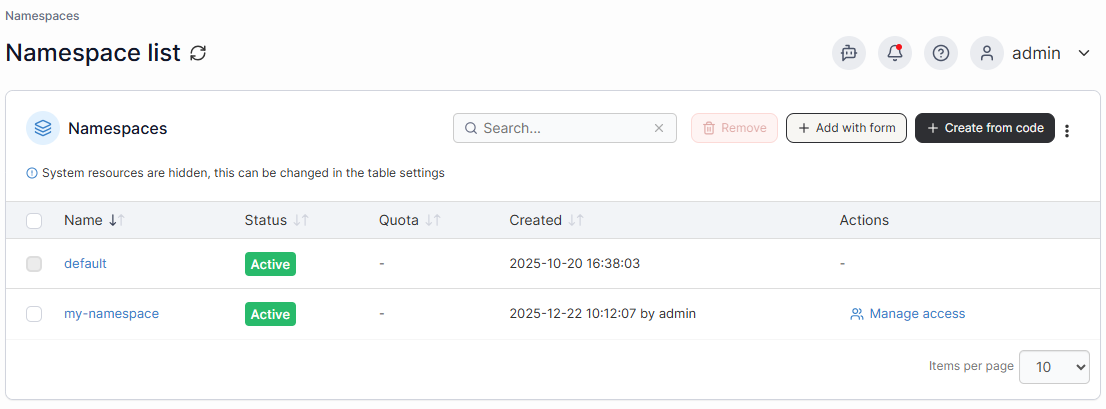
Policy Enforcement and Configuration Safety
Most Kubernetes security issues come from configuration mistakes. Effective Kubernetes security solutions apply policies, image controls, and safe defaults to block risky deployments early. These guardrails reduce manual reviews and production incidents.
Portainer adds practical controls that block risky actions while still respecting existing workflows.
Visibility, Auditing, and Accountability
Security teams need clear answers when something changes. Audit logs, activity tracking, and historical visibility are essential features in mature Kubernetes security tools. These capabilities reduce investigation time and alert fatigue.

Portainer provides detailed audit trails that show who did what, where, and when.
Control Without Blocking Expert Workflows
Your Kubernetes security tool should support your engineers, not slow them down. Choose a tool that lets your team continue using CLI tools and kubeconfig files when needed. Portainer respects this balance by adding governance on top of existing workflows rather than replacing them.
Book a demo now and gain firsthand experience of how your team can secure Kubernetes clusters smarter and easier.
Secure Kubernetes with Portainer
In most enterprise teams, Kubernetes security does not fail because of attackers. It fails because too many people have access, changes happen outside the process, and no one can quickly answer what changed when an incident occurs.
Portainer solves this problem by restoring control through clear access boundaries, enforced governance, and full auditability. It does this by acting as a secure control layer that governs how teams access clusters, deploy workloads, and make changes, without forcing engineers to abandon current Kubernetes workflows.
Contact our sales team to see how Portainer provides built-in Kubernetes security for enterprises.





