GitOps tools promise safer, more consistent Kubernetes operations. But in reality, not every team wants (or needs) to manage everything through Git alone.
That leaves a common question: do you commit fully to GitOps, or is there a more flexible way to operate?
In this guide, we provide the answer, breaking down ArgoCD, FluxCD, and Portainer. You’ll see where each fits, how they differ in day-to-day workflows, and why many DevOps teams and engineers use them together instead of choosing just one.
First, let’s compare the tools side by side.
Portainer vs ArgoCD vs FluxCD at a glance
Overview
Feature comparison
Now, let’s discuss the tools at length.
An overview of Portainer
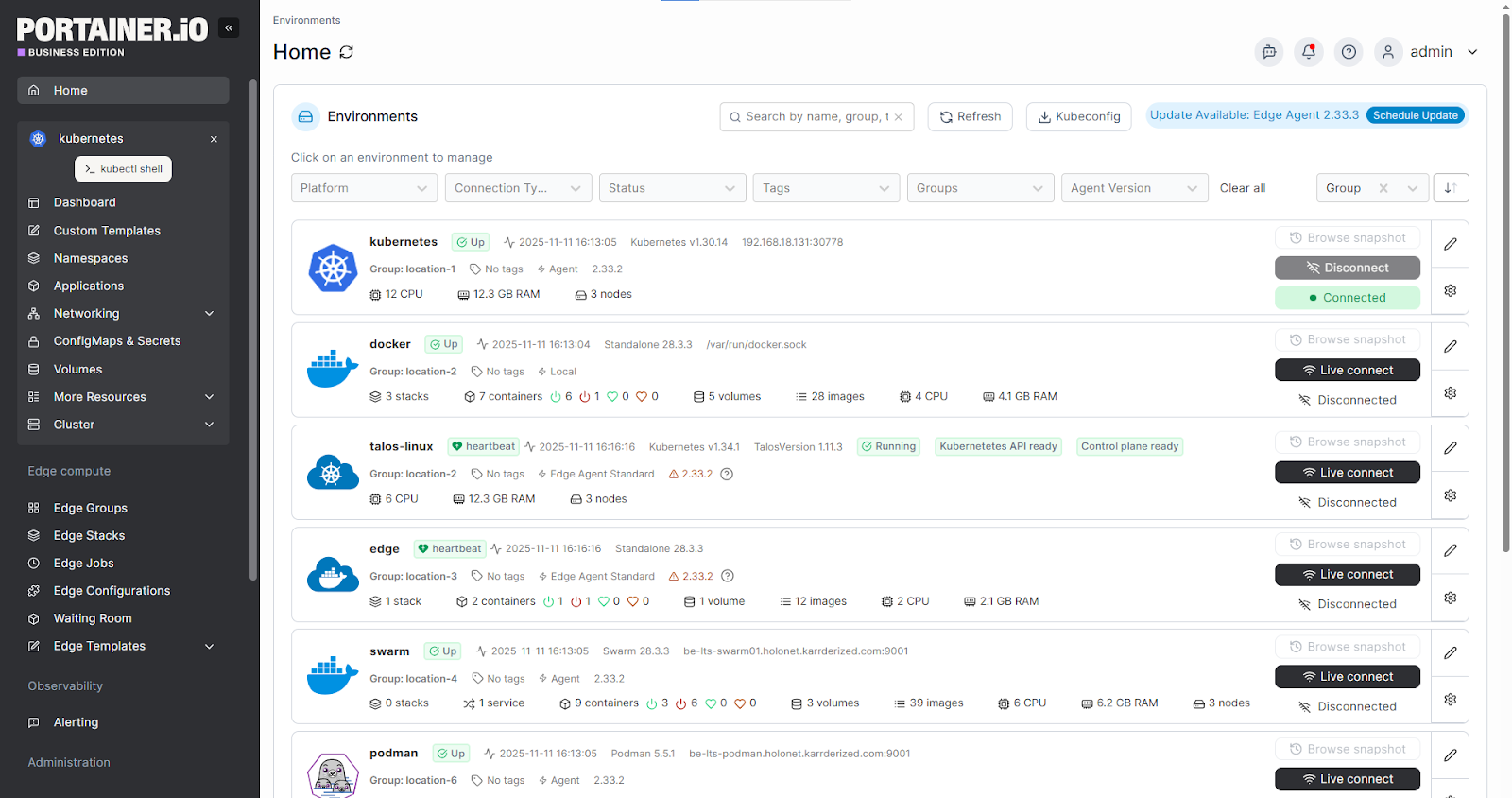
Portainer is an easy-to-use container and Kubernetes management platform. It is built for teams that need clear, practical control of their environments without going all-in on a Git-only operating model.
While ArgoCD and FluxCD focus on how changes are delivered, Portainer focuses on how environments are operated.
Think:
- Visual cluster management
- Workload visibility
- Role-based access control

- Safe changes across Docker and Kubernetes
As a result, Portainer is the flexible middle ground. It supports GitOps workflows when it makes sense for teams. More importantly, it comes with UI and operational controls for on-prem, cloud, and edge environments.
{{article-cta}}
An overview of ArgoCD
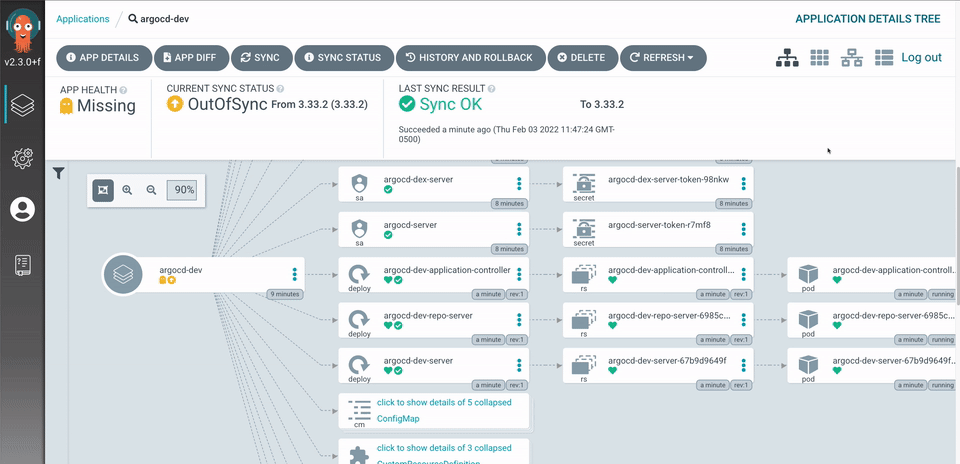
ArgoCD is a dedicated GitOps continuous delivery tool built specifically for Kubernetes. It treats Git as the single source of truth and continuously reconciles live clusters against declared application state in repositories.
AgroCD’s strengths lie in advanced GitOps automation:
- Application health monitoring
- Diffing and drift detection
- Automated rollbacks
- Support for managing many applications across multiple clusters
These capabilities make it well-suited for organizations running large, complex Kubernetes environments. It is also ideal where strict consistency and automation are required.
However, there are some tradeoffs. ArgoCD assumes Git-driven workflows end-to-end. This can feel heavy for teams that want operational flexibility alongside GitOps rather than everything enforced through Git alone.
An overview of FluxCD
FluxCD is a Kubernetes-native GitOps tool. It is built around the idea that everything in your cluster should be declared and reconciled from “Git.”
So, instead of acting as a separate control plane, Flux runs inside the cluster and uses controllers to continuously apply and enforce the desired state defined in repositories.
Flux strength is its deep alignment with Kubernetes primitives. As such, it relies on:
- Declarative configuration
- Native APIs
- Composable controllers
In short, Flux is ideal for DevOps teams and engineers who operate close to Kubernetes internals and want a pure, Git-first workflow. However, it has a steep learning curve compared to tools designed to abstract day-to-day operations behind a UI.
Portainer vs ArgoCD vs FluxCD: who is each best for?
Often, these tools are compared, but they are built for different operating styles. Below, we clarify when each tool is ideal, based on team size, workflow maturity, and the degree of GitOps control needed.
Who is Portainer best for?
Portainer fits teams that want clear operational control without GitOps complexity. It suits smaller teams, platform engineers, and operators who need visibility, access control, and workload management across Kubernetes, Docker, and mixed environments.
Instead of forcing everything through Git, Portainer supports GitOps where it makes sense while still offering a UI for day-to-day tasks (such as troubleshooting, Kubernetes RBAC, and multi-cluster management). It’s a strong fit when simplicity, speed, and flexibility are more crucial than enforcing a strict Git-only model.
Who is ArgoCD best for?
Argo CD is ideal for organizations running large, complex Kubernetes estates that want a rigorous GitOps workflow. Teams that need automated rollbacks, continuous reconciliation, and detailed application health monitoring tend to benefit most.
It works well in environments where Git is the single source of truth and changes must follow tightly controlled pipelines. That power comes with added operational overhead, making ArgoCD better suited for teams with dedicated platform expertise and mature GitOps practices.
Who is Flux CD best for?
Flux CD fits teams that prefer a Kubernetes-native, Git-first approach without a separate UI layer. It’s commonly used by engineers who are comfortable working close to Kubernetes APIs and want declarative automation driven entirely from Git repositories.
Flux is lightweight, composable, and flexible, making it a good choice for Kubernetes-centric teams that value control and extensibility over ease of use. For less experienced teams, however, the lack of a built-in UI can increase the learning curve.
Portainer, ArgoCD, and FluxCD: How they compare in practice
Rather than competing head-to-head, these tools solve different layers of the Kubernetes problem. Let’s break it down.
ArgoCD and FluxCD: GitOps Specialists
Argo CD and Flux CD are designed around a clear principle: Git is the single source of truth. They continuously reconcile cluster state against Git repositories, making them ideal for teams that:
- Want strict, automated enforcement of the desired state
- Operate mature CI/CD pipelines
- Are comfortable resolving drift entirely through Git workflows
They excel at continuous delivery, but assume strong Git discipline and operational maturity.
Portainer: Operational control with GitOps support
Portainer approaches the problem from the opposite direction: operational clarity first. It provides a centralized control plane for Kubernetes environments, combining:
- Visual workload and cluster management
- Role-based access control and guardrails
- Optional Git-based deployment flows
This makes Portainer especially effective for teams that want GitOps (where and when crucial), without forcing every operational task through pull requests.
The real-world pattern: Complement, don’t Replace
In “real” environments, these tools often coexist:
- Argo CD or Flux CD handles continuous Git-driven deployments
- Portainer manages access, visibility, approvals, and operational workflows around them
Book a demo now to try Portainer out!
Benefits and Limitations of Each Platform
We established that the tools work together. Nonetheless, you still need to learn about their strengths and differences. This will help you decide how strongly you want to enforce GitOps, and how much operational overhead your team can realistically support.
Portainer
Portainer’s biggest strength is operational simplicity. It’s designed for teams that need clear visibility and control over containers and Kubernetes clusters without committing to a Git-only workflow.
Instead of assuming everything flows through pull requests, Portainer supports a mix of approaches:
- Manual operations
- UI-driven workflows
- Git-based deployments where they make sense
That makes Portainer especially useful for small to mid-sized teams, platform engineers, and operators managing diverse environments (on-prem, cloud, edge, and hybrid).
Furthermore, Portainer makes managing day-to-day tasks seamless with its single interface. For many teams, this reduces cognitive load and speeds up operations without sacrificing control.
Portainer also supports GitOps-style workflows, but intentionally avoids the deeper automation layers found in specialized GitOps tools. This aligns with teams that want Git as a delivery mechanism, not as the only way to operate Kubernetes.
Benefits
- Low operational overhead: Intuitive UI and RBAC reduce reliance on YAML-heavy workflows
- Broad platform support: Works across Kubernetes, Docker, and mixed environments
- Flexible workflows: GitOps (where & when useful); UI and APIs (where & when faster)
- Strong day-to-day ops focus: Visibility, access control, and cluster management in one place
Limitations
- Not a full GitOps engine: Lacks advanced automation like continuous reconciliation loops and complex rollout strategies
- Less suited for Git-only orgs: Teams enforcing strict GitOps everywhere may prefer Argo CD or Flux CD
Community insight
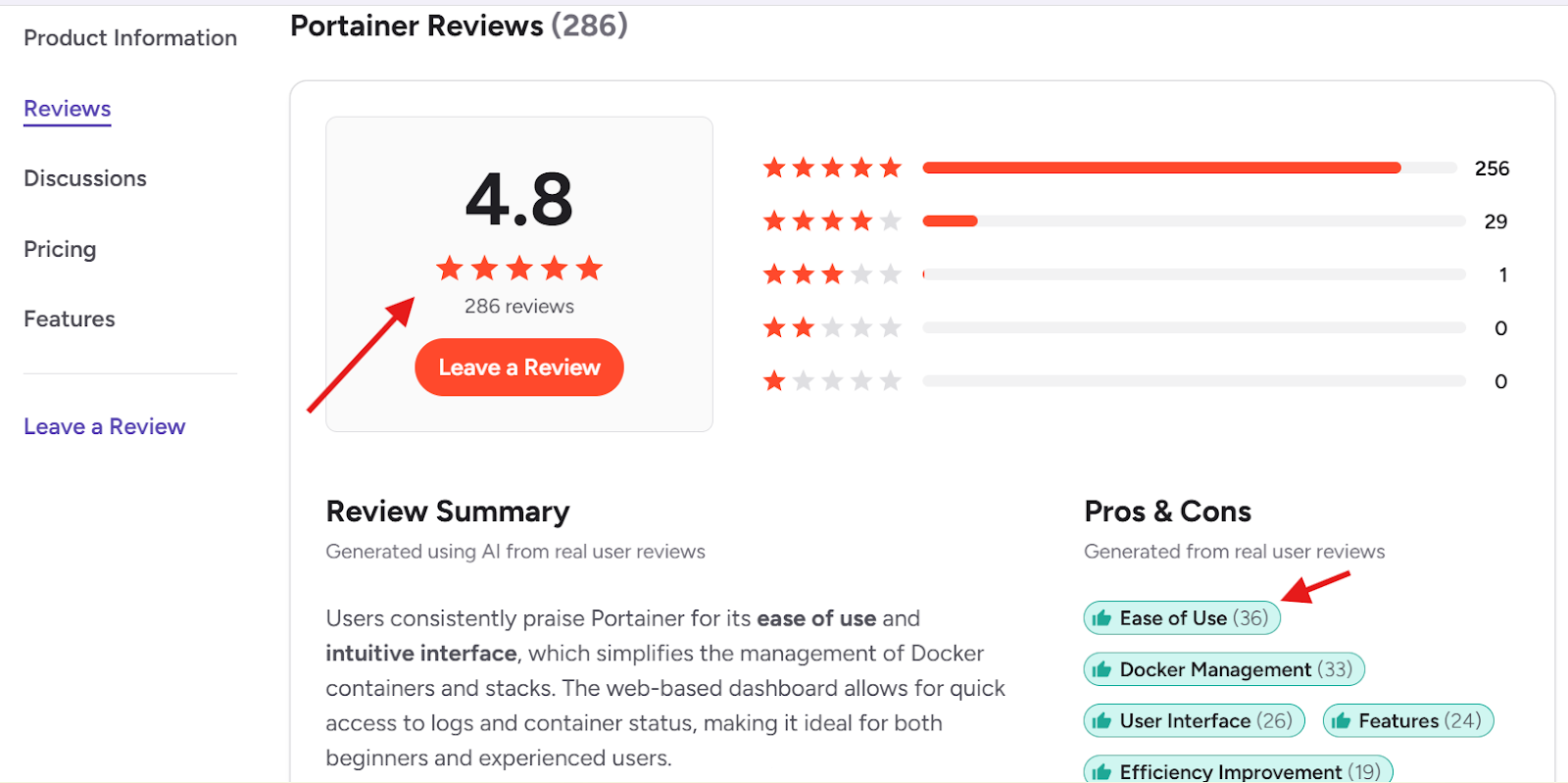
With a 4.8 rating (from 286 reviews) on G2, Portainer consistently receives high marks for ease of use and operational clarity. This reflects its focus on practical Kubernetes management rather than maximum GitOps depth.
ArgoCD
ArgoCD is a full-featured GitOps continuous delivery tool for Kubernetes, designed to automate deployments at scale. It continuously reconciles your cluster state against the desired state defined in Git. This provides a path to consistency and repeatability.
As a result, Argo is a strong choice for large, distributed environments with multiple clusters and complex delivery requirements.
Benefits
- Automated reconciliation and drift detection: ArgoCD continuously watches Git repos and enforces the desired state. This way, it prevents future configuration drift and manual errors.
- Application health and visibility: Built-in dashboards and CLI/API tools show real-time status and simplify oversight.
- Scales across clusters: It can deploy and monitor apps across many clusters from a single control plane, which is why organizations manage hundreds of apps under Argo CD.
- Advanced GitOps integrations: It supports Helm, Kustomize, multi-cluster projects, and RBAC/SSO. That comes in handy for enterprises with strict change control.
Limitations
- Steep learning curve: ArgoCD assumes familiarity with GitOps principles, CRDs, and Kubernetes manifests. As such, the onboarding and configuration can be challenging without dedicated expertise.
- Operational overhead: Running and tuning a centralized control plane can consume notable resources, especially in large setups.
- Complex workflows: Users on community forums note that integrating dynamic parameters or secrets into Git workflows can complicate the GitOps “single source of truth” ideal.
- Narrow focus: It excels at continuous delivery via Git, but teams still need other tools for pre-deployment testing, security scanning, or broader CI/CD orchestration.
Community insight
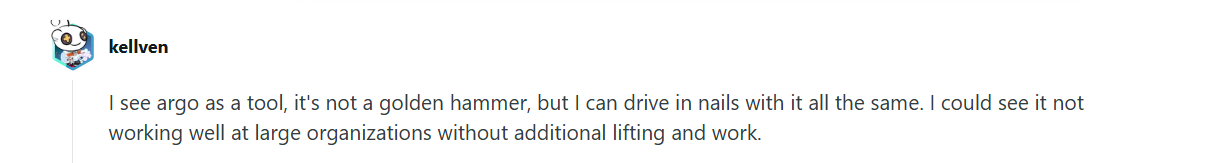
Users appreciate Argo CD’s automation but also highlight real-world complexity, especially around multi-branch setups and environment promotions. Kellven on Reddit summarized it:
Overall, Argo CD’s strengths shine when scale, strict GitOps enforcement, and automation across clusters are a priority. But note its learning curve and platform demands before committing to it as the central delivery mechanism.
FluxCD
FluxCD is a Kubernetes-native GitOps engine built around the idea that your cluster should always reflect what’s declared in Git. It runs inside the cluster as a set of controllers that continuously watch repositories and apply changes automatically. This deep integration with Kubernetes APIs makes Flux feel like an extension of Kubernetes itself rather than an external overlay.
Benefits
- Tight Kubernetes alignment: Flux uses native APIs and custom resources to apply changes, making it feel natural to teams comfortable with Kubernetes internals.
- Continuous automatic reconciliation: Once configured, Flux actively ensures that the live state matches the Git state without extra triggers.
- Modular and extensible: Flux’s design “mixes and matches” controllers for alerts, notifications, and image automation. This could be useful if your setup relies on them.
- Declarative configuration: All desired state lives in Git, reducing the risk of hidden drift and manual overrides.
Limitations
- Kubernetes-centric only: Flux is focused on Kubernetes; it doesn’t manage non-Kubernetes platforms, limiting its use in mixed environments.
- Steeper entry for beginners: Teams new to GitOps or Kubernetes CRDs may find the initial setup and concepts (custom resources, controllers, reconciliation loops) more difficult to grasp than UI-based alternatives.
- Minimal built-in UI: Unlike tools with integrated dashboards, Flux relies primarily on Git and CLI/third-party UIs, which can slow everyday workflows for some teams.
- Operational overhead: Running multiple controllers and automations inside clusters adds maintenance responsibilities, especially in multi-cluster setups.
Community insight
Users on Reddit note Flux’s power but also its learning curve. And the latter is a recurring theme for image automation and multi-environment promotion workflows.
In summary, Flux is ideal if you want a pure, declarative GitOps workflow tightly woven into Kubernetes. But you should be prepared for deeper platform engagement and fewer UI-driven shortcuts than other tools offer.
Also read: Kubernetes Orchestration & Management Tools in 2026
Understanding Where Each Platform Fits
TL;DR:
Portainer vs ArgoCD vs FluxCD: Final Thoughts
There’s no single “best” GitOps tool. So, instead, focus on your team’s maturity and goals.
- Argo CD and Flux CD shine when you need deep, automated GitOps at scale.
- If clearer visibility, safer day-to-day operations, and GitOps (where it adds value, not overhead) are the goal, go for Portainer.
Book a demo now to see how Portainer supports practical GitOps and everyday Kubernetes operations!





