Developer Self Service
Access for your whole team, but only to what they need.
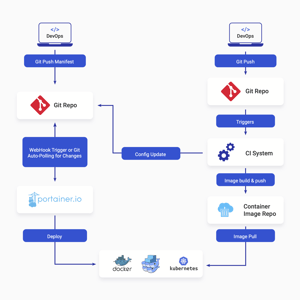
Configuring a containerized environment, whether it be Docker, Swarm, Kubernetes, or Nomad, can be complicated. What makes it even more complicated is managing it and providing access to others in your company that need to use it, but without providing everyone full admin access to everything.
Those complications can disappear with Portainer. With the controls you need to configure and manage your environments, you can get up and running quickly and efficiently, without needing to learn the orchestrators in depth. Then, using Portainer’s RBAC functionality you can give your users and teams access to the environments they need with the capabilities they require, without compromising security.
Whether you’re running one Docker Standalone instance or multiple orchestrator clusters - or anything in between - Portainer can help.
Centrally manage your users and groups by integrating your existing auth provider with Portainer, including auto syncing access.
Portainer’s intuitive interface lets you get your deployments up and running without having to spend time learning the platforms.
With our RBAC functionality, you can give your users access to your environments, but only to the functions they need.
Keep an eye on how your nodes and clusters are performing, and configure resource limits to make sure your apps get what they need to run.
Portainer keeps authentication and activity logs, tracking everything that happens through Portainer so you know what’s going on.
How does Portainer work as a developer portal?
Imagine you have a number of environments spread across a range of providers as well as on-premise, and a mix of orchestrator platforms including Docker Swarm and Kubernetes. You want to give your team access to these environments but don’t want to have a separate login system, individual management interfaces, or to give your users full access to everything.
With Portainer, you can give your team a single system to log into for all your environments, regardless of their type or location, with access provided by your existing authentication system. Each user and group can be configured with access to only the environments and functions they need - for example, read only access for helpdesk staff, access to staging but not production for junior devs, operational control for team leads, and more.
As a result, your team can quickly get access to deploy, maintain and troubleshoot your applications and environments as needed, without the headaches and security implications of other approaches.